Pentester Academy – Cloud Security AWS Bootcamp
English | Tutorial | Size: 3.6GB
Most AWS deployments are breached by a common set of vulnerabilities which attackers repeatedly use. In 5 modules, this bootcamp teaches you to identify, exploit and secure vulnerabilities in the 5 most commonly used AWS components, so you can be a job-ready Cloud Security practitioner.
Recordings of this bootcamp are now available as part of our annual subscription. Subscribe to enjoy:
Access to all on-demand bootcamps and relevant labs, including this one
2000+ hands-on labs covering another 130+ subtopics
What You’ll Learn
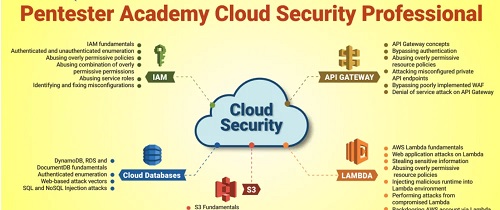
The syllabus of this bootcamp focuses on the teaching you the fundamentals and exploits for the 5 most commonly used components in AWS deployments:
1. Identity and Access Management (IAM)
2. API Gateway
3. Lambda
4. Cloud Databases
5. Simple Storage Service (Amazon S3)
Module I: Identity and Access Management (IAM)
Introduction to IAM
IAM users, roles and groups
Temporary security credentials
Policies and permissions
Policy evaluation logic
IAM access analyzer
Enumerating IAM users and roles
Cross-account AWS roles and user enumeration
Abusing overly permissive IAM trust policies
Escalating privileges by abusing IAM policies and permissions
Module II: API Gateway Attack-Defense
Introduction to API Gateway
Enumerating API Gateway and API keys
Understanding stage variables and usage plans
Authorization with lambda authorizers
Bypassing authentication by verb tampering
Abusing overly permissive resource policies
Attacking misconfigured private API endpoints
Bypassing poorly implemented WAF
Performing Denial of Service attack on API Gateway
Module III: Serverless Functions: Lambda
Introduction to AWS Lambda
Lambda functions
Lambda applications
Lambda layers
Lambda alias routing
Custom runtimes
Enumerating Lambda functions and layers
Event data injection
Command injection
Function runtime code injection
XML external entity (XXE)
Server-side request forgery (SSRF)
Object deserialization attacks
SQL injection
NoSQL injection
Abusing overly permissive resource policies
Abusing AWS Lambda permissions
Manipulating function execution flows
Retrieving application secrets, keys, and credentials
Retrieving sensitive information from Lambda Runtime API
Exploiting vulnerable component and custom runtimes
Abusing temporary and shared file systems
Maintaining access on an AWS account (backdoor)
Module IV: DynamoDB and other Cloud Databases
Introduction to DynamoDB
Tables, indexes, and streams
Partition key and sort key
CRUD operations
PartiQL support
NoSQL injection attack on a DynamoDB-based application
SQL injection attack through PartiQL support on a DynamoDB-based application
NoSQL injection attack on a MongoDB-based application
SQL injection attack on an RDS-based application
Module V: Cloud Storage: S3 Misconfigurations
Introduction to S3
S3 ransomwares
Bucket and objects
Object metadata and versioning
IAM policies, bucket policies, and access control lists
Server-side encryption and client-side encryption
Object locking
Pre-signed URLs
Access analyzer for S3
Enumerating public S3 buckets
Identifying bucket policy/ACL constraints on an S3 bucket
Identifying anonymous write operations on an S3 bucket
Leveraging misconfigured bucket policies and ACPs
Anonymous/Authorized public read
Reading policies and identifying object names
Writing objects to buckets
Overwriting bucket ACL and object ACL
Overwriting bucket policies
Performing denial of service
Identifying writable buckets without performing write operations
Chaining web application attacks through S3 resources
Meet the instructor
Jeswin Mathai
He has published his work at DEFCON China, RootCon, Blackhat Arsenal, and Demo labs (DEFCON). He has also been a co-trainer in classroom trainings conducted at HITB, RootCon, OWASP NZ Day. He has a Bachelor degree from IIIT Bhubaneswar. He was the team lead at InfoSec Society IIIT Bhubaneswar in association with CDAC and ISEA, which performed security auditing of government portals, conducted awareness workshops for government institutions. His area of interest includes Malware Analysis and Reverse Engineering, Cryptography, WiFi security, and Web Application Security.

RAPIDGATOR
rapidgator.net/file/ced2f036eda18a86d277de4b4432ded2/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part1.rar.html
rapidgator.net/file/7495f9db2c56fd10e6686edc1da5a07a/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part2.rar.html
rapidgator.net/file/1f2bce9b6b93c9c943de480046537e7a/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part3.rar.html
rapidgator.net/file/52c91caf92732a4dfaf715c69357daa2/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part4.rar.html
rapidgator.net/file/51303a9a1c2858cc3c129376241d35c1/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part5.rar.html
rapidgator.net/file/568ab32c5d8709de865b9384e9e320d0/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part6.rar.html
NITROFLARE
nitroflare.com/view/A896C3B9CDD73A4/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part1.rar
nitroflare.com/view/07387A536A92E88/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part2.rar
nitroflare.com/view/F7F0F5101143C02/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part3.rar
nitroflare.com/view/41B44A57A057B39/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part4.rar
nitroflare.com/view/F65A3D93D91EA5D/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part5.rar
nitroflare.com/view/1572C2A0214DDE9/PentesterAcademy_-_Cloud_Security_AWS_Bootcamp.part6.rar