O`Reilly – Kubernetes Security Attacking and Defending Kubernetes-iLLiTERATE
English | Tutorial | Size: 809.68 MB
Like many complex systems Kubernetes has historically been insecure by default, and contains a number of “footguns” that make secure deployments difficult. Segregation of duty, least privilege, and a rigorous Continuous Security approach are the foundations of any secure system-however these become more difficult to achieve in distributed systems with many moving parts.
But all is not lost! With an understanding of the foundational layers and principles including micro-segmentation, zero trust, and local PKI, Kubernetes can be secured against the most ardent of attackers.
The course guides attendees through an introduction to Linux container security, and progresses to advanced Kubernetes cluster security. It emphasizes pragmatic threat modelling and risk assessment based on an understanding of the tools and primitives available.
What you’ll learn and how you can apply it
By the end of this course, you’ll understand:
Linux and container security
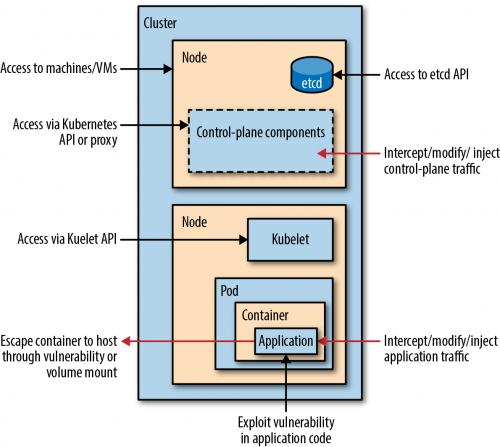
The Kubernetes attack surface
Automated container security testing and DevSecOps workflows
Open Source security tooling and the vendor landscape
And you’ll be able to:
Break out of a container
Attack and harden Kubernetes
Security test Kubernetes clusters
You’re an intermediate to advanced Kubernetes user who wants to strengthen their security understanding
You want to become an SRE, DevOps, or DevSecOps engineer
Prerequisites
Familiarity and comfort with Docker, Kubernetes, and the Linux command line
Recommended preparation:
Make sure that you have a Linux VM or physical machine with at least 8GB of RAM and 20GB of disk space, as well as a second machine (or VM) with a Linux terminal. You are welcome to follow along within these, but you will need both Linux machines in order to fully participate in the exercises.
Read Kubernetes: Up and Running (book), Chapter 1. Introduction
Read Kubernetes Security (report)
Chapter 1. Approaching Kubernetes Security
Chapter 6. Running Containers Securely
PEARSON OOWNS MAANY EDU BRAANDS INKLUDINNG
ADDISON-WESLEY PEACHPIT PRENTICE-HALL ECOLLEGE
AND MAANY MORE!
WEE ASUMME NO LIIABILLITY FUR A WROONG SPELING
COZ WEE ARRE A NON (iL)LiTERATE GRUP!!
TANNKS TU THE LITERATE ASKII FRIIEND!!

RAPIDGATOR
rapidgator.net/file/9d0fa1ab0608ba606ee7772be3675ec4/OREILLY_KUBERNETES_SECURITY_ATTACKING_AND_DEFENDING_KUBERNETES-iLLiTERATE.part1.rar.html
rapidgator.net/file/c72b312c31de1b7c2468321a88a0dd21/OREILLY_KUBERNETES_SECURITY_ATTACKING_AND_DEFENDING_KUBERNETES-iLLiTERATE.part2.rar.html
UPLOADGIG
uploadgig.com/file/download/3108403b9bfA3684/OREILLY_KUBERNETES_SECURITY_ATTACKING_AND_DEFENDING_KUBERNETES-iLLiTERATE.part1.rar
uploadgig.com/file/download/024c6c6f2b0C4311/OREILLY_KUBERNETES_SECURITY_ATTACKING_AND_DEFENDING_KUBERNETES-iLLiTERATE.part2.rar