Cloud Academy – Getting Started with Azure Virtual Machines {2020}
English | Size: 1.12 GB
Category: Tutorial
This course will give you a basic understanding of Azure virtual machines (VMs) and how you can use them in your Azure environments.
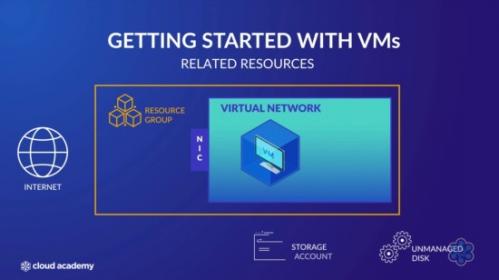
The course begins by introducing you to Azure VMs and what resources are necessary to deploy them, before moving onto pricing and the different virtual machine options available. Next, the course explores availability sets and availability zones and gives a demonstration that shows you how to create an availability set using the Azure portal.