Linkedin Learning – Microsoft 365 Implement Security and Threat Management-ZH
English | Size: 398.73 MB
Category: Tutorial
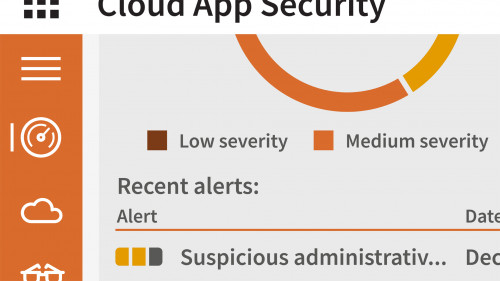
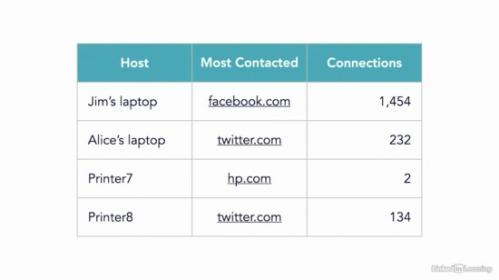
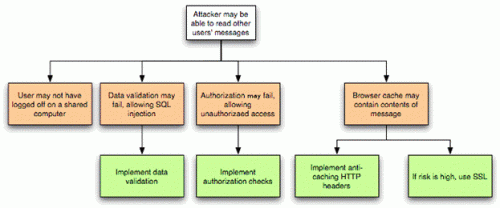
The Microsoft 365 Mobility and Security (MS-101) exam tests a candidates ability to evaluate, plan, migrate, deploy, and manage Microsoft 365 services. The second domain of the exam covers the implementation, management, and monitoring of threat management and security protection services. This course covers these objectives, outlining the recommended tools and techniques to ensure user accounts and access are managed and controlled correctly. Learn how to implement and manage Cloud App Security, Office 365 Advanced Threat Protection (ATP), Windows Defender ATP, Azure AD Identity Protection, and additional security reports and alerts. By the end of the course, youll have the skills to secure your Microsoft 365 deployments and ace the second domain of this critical certification exam