
Udemy – Reverse Engineering and Software Protection
English | Size: 1.33 GB
Category: Tutorial
Reverse Engineering and Software Protection
Learn how software protection works from the inside out using the x64dbg debugger

Udemy – Reverse Engineering and Software Protection
English | Size: 1.33 GB
Category: Tutorial
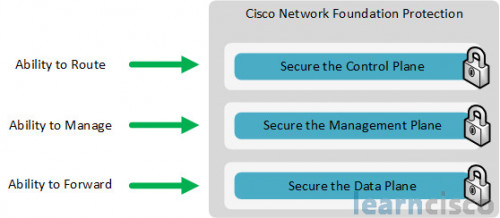
INE – Network Foundation Protection Control Plane
English | Size:2.08 GB
Category: Networking

INE – Network Foundation Protection Data Plane
English | Size: 1.88 GB
Category: Cisco | Networking | Security
PluralSight – Design A Data Protection Strategy With Microsoft Azure FEB2020 Update-REBAR
English | Size: 253.56 MB
Category: Tutorial
Understanding all the aspects of data protection and addressing can be complex. In this course, Design a Data Protection Strategy with Microsoft Azure, you will learn the foundational knowledge necessary to design a data protection strategy using Azure services. First, you will learn key considerations related to data protection. Next, you will discover encryption options for all stages of the data lifecycle. Finally, you will explore how to add performance and availability requirements for data in Microsoft cloud services. When you’re finished with this course, you will have the skills and knowledge of data protection needed to design a strategy for your organization’s data in Microsoft Azure.