Ethical Leadership | Cybrary
English | Size: 10.29 GB
Category: Tutorial
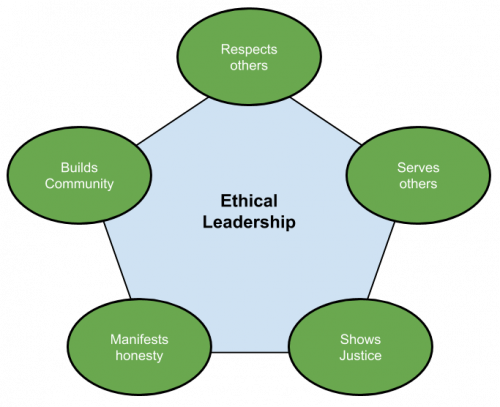
Ethical leaders realize every decision they make affects others. When acting with ethical leadership, leaders can focus on what’s right, not just who is right. But deciding on what’s right depends on context, the company’s culture, and other factors.