INE – Perimeter & Network Security Engineering
English | Tutorial | Size: 2.87 GB
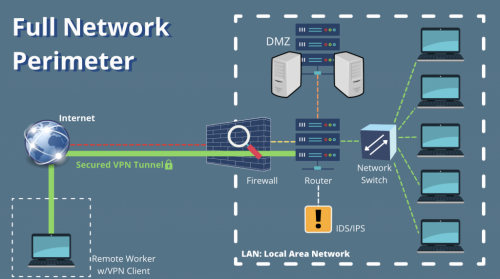
The perimeter of a network is often the most attacked area, and sometimes the most overlooked. With the introduction of even more cloud-hosted resources, this line is becoming more blurred every day. In addition, a properly secured internal network is a key backbone to an overall secure IT infrastructure. This course will introduce you to properly configuring and securing not only the network perimeter, but also your internal network infrastructure. We’ll start with edge firewalls, and work all the way through switches, routers, wireless infrastructure, printers, and more. Learn not only how to secure your network, but also WHY certain security practices are needed.

RAPIDGATOR
rapidgator.net/file/1d2120ee32491619b9a35bf32cd23e4e/_INE_-_Perimeter_&_Network_Security_Engineering.part1.rar.html
rapidgator.net/file/38dc21a8e3cc2dd2c4072ccb71212999/_INE_-_Perimeter_&_Network_Security_Engineering.part2.rar.html
rapidgator.net/file/6c649fd91b8e3c9565082603fa0088be/_INE_-_Perimeter_&_Network_Security_Engineering.part3.rar.html
rapidgator.net/file/06595d44b76213029be5b3aa856a5610/_INE_-_Perimeter_&_Network_Security_Engineering.part4.rar.html
rapidgator.net/file/da61b3646bcc4b895147f72e238bb976/_INE_-_Perimeter_&_Network_Security_Engineering.part5.rar.html
NITROFLARE
nitroflare.com/view/82756685FABA17D/_INE_-_Perimeter_%26_Network_Security_Engineering.part1.rar
nitroflare.com/view/40355B691A68444/_INE_-_Perimeter_%26_Network_Security_Engineering.part2.rar
nitroflare.com/view/89354DE9A91FB68/_INE_-_Perimeter_%26_Network_Security_Engineering.part3.rar
nitroflare.com/view/E3AC9F62D174CE4/_INE_-_Perimeter_%26_Network_Security_Engineering.part4.rar
nitroflare.com/view/EFC0824E81DF34D/_INE_-_Perimeter_%26_Network_Security_Engineering.part5.rar