Cyber Security Source Code Defender (CSCD)
English | Size: 1.38 GB
Category: E-learning | HACKING | Security | others
About the Cyber Security Source Code Defender Certificate:
The Cyber Security Source Code Defender is a knowledge-based certificate offered by CSTT. As part of CCTT certificate program, the certificate is particularly relevant for recent college/university graduates and professionals in IT space, and those looking for a career change to cybersecurity.
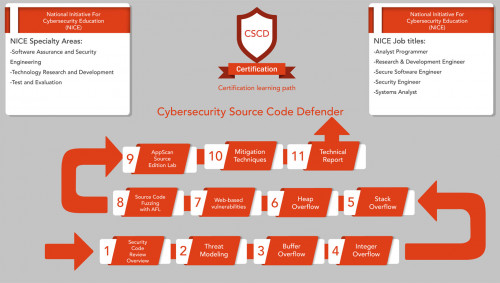
The certificate is aligned with the National Institute of Standards and Technology (NIST) National Initiative for Cybersecurity Education (NICE), which is compatible with global cybersecurity issues, activities and job roles. The certificate is also aligned with the Skills Framework for the
Information Age (SFIA). The Cybersecurity Fundamentals Certificate does not have an expiration date.
Overview:
In enterprise IT, there is a single point where everything that matters in information, technology and business converges: Cyber Security Think Tank (CSTT), a new security knowledge platform and professional program. CSTT is helping shape the future of cybersecurity through cutting-edge thought leadership, as well as training and certification programs for the professionals who are leading it there. Building on the strength of globally-recognized expertise, it gives cybersecurity professionals a smarter way to keep organizations and their information more secure.
With CSTT, business leaders and cyber professionals can obtain the knowledge, tools, guidance and connections to be at the forefront of a vital and rapidly changing industry. Because Cyber Security Think Tank (CSTT) is at the center of everything that’s coming next.
Who’s it For:
Analyst Programmer
Research & Development Engineer
Secure Software Engineer
Security Engineer
Systems Analyst
Application Security Tester
Security Systems Engineer
Testing and Evaluation Specialist
What You’ll Learn
Understand Threat Modeling
Learn Microsoft Security Development Lifecycle
Identify multiple vulnerabilities in applications’ source code
Learn different techniques to find bugs: Manual, Scanning ,Fuzzing
Practice with best commercial source code scanners in the market
Confirm the vulnerability by replicating the bug in the Lab
Syllabus:
Security Code Review Overview
Introduction
Compliance
Threat Modeling
Introduction
Decompose the Application
Determine and Rank Threats
Mitigation Strategy
Buffer Overflow
Overview
Integer Overflow
Overview
Finding the Bug: Lab
Verifying the Bug: Lab
Mitigation Techniques: Lab
Stack Overflow
Overview
Finding the Bug: Lab
Verifying the Bug: Lab
Mitigation Techniques: Lab
Heap Overflow
Overview
Finding the Bug: Lab
Verifying the Bug: Lab
Mitigation Techniques: Lab
Web-based vulnerabilities
Introduction
SQL Injection
Finding the Bug: Lab
Verifying the Bug: Lab
Mitigation Techniques: Lab
Cross-Site Scripting
Finding the Bug: Lab
Verifying the Bug: Lab
Mitigation Techniques: Lab
File Inclusion:
Finding the Bug: Lab
Verifying the Bug: Lab
Mitigation Techniques: Lab
Directory Traversal
Source Code Fuzzing with AFL
Running AFL Fuzzer: Lab
Crash Analysis: Lab
Verifying the Bug: Lab
AppScan Source Edition Lab
Mitigation Techniques
Technical Report
DOWNLOAD:

https://rapidgator.net/file/1ba6435a68b170bc05f5c968efde62d6/CSSCD.part1.rar.html
https://rapidgator.net/file/c2b05d50ca5fa00a59f25bd2a4e13e66/CSSCD.part2.rar.html
https://rapidgator.net/file/cb11a1a61e86b561a1f1eca1fb44917e/CSSCD.part3.rar.html

https://nitroflare.com/view/F1FB2B3C7577C24/CSSCD.part1.rar
https://nitroflare.com/view/E5C02C53A1D8D66/CSSCD.part2.rar
https://nitroflare.com/view/54922F1199CB686/CSSCD.part3.rar