![[Update Links] PHP Design Patterns | Pluralsight](https://i.imgur.com/Ac7dM8i.png)
English | Size: 187.41 MB
Genre: eLearning
![[Update Links] PHP Design Patterns | Pluralsight](https://i.imgur.com/Ac7dM8i.png)
Lynda – Software Design From Requirements to Release-APoLLo
English | Size: 246.25 MB
Category: Tutorial
PluralSight – Advanced Network Security on AWS-ELOHiM
English | Size: 132.93 MB
Category: Tutorial
INE – IOS XR Overview
English | Size: 756.6 MB
Category: Cisco | Networking
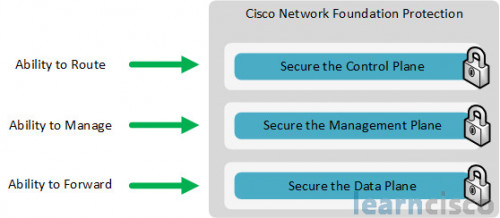
INE – Network Foundation Protection Control Plane
English | Size:2.08 GB
Category: Networking